What Is Two-Factor Authentication, And Why Should Your Business Use It?
- Anthony
- February 15, 2018
- 10:01 AM
- No Comments
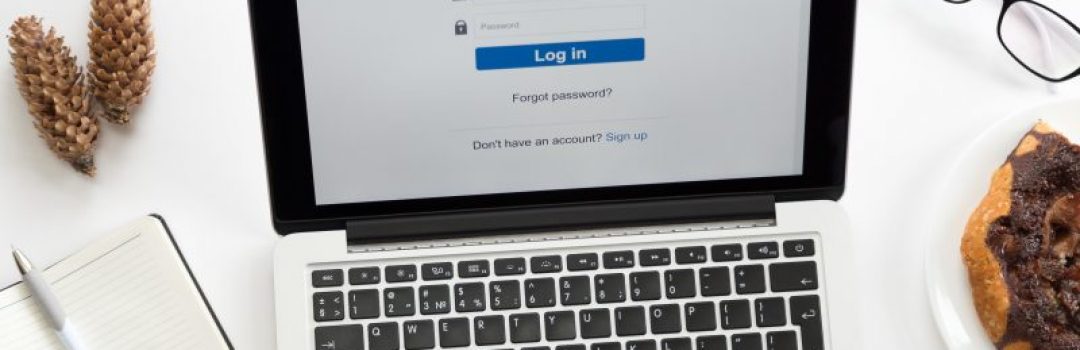
Two-factor authentication offers an extra level of cyber security that no business should be without. But what is it, how does it work, and how can you use it in your own business?
Simply put, two-factor authentication is a system of confirming a person’s identity, using two different methods. Usually, this consists of a traditional password, combined with a device of some sort - in other words, something the user knows and something the user has.
For example, if you use Microsoft’s two-factor authentication, you’ll find that simply entering your password will no longer be sufficient to log into your Microsoft’s account. You’ll also be required to supply a unique verification code, which you can only get from the Microsoft Authenticator app.
Available for all popular mobile operating systems, Authenticator constantly generates these codes, updating every 30 seconds. Enter an expired code into your Microsoft login page, and it won’t grant you access. Do it within the current 30-second window, and the login will work.
What’s particularly important is that you register your phone with Microsoft first. While in the Authenticator app, you have to scan a unique barcode, which you’ll find in the security settings of your online account. This then links Authenticator and your phone to your account. From then on, the authentication codes will only be sent to that app on that device.
The security benefit of such a system should be clear. If someone wants to log into your account, then they’ll not only need your password, but your phone too.

Is Two-factor Authentication Foolproof?
No system is 100% safe, and two-factor authentication is no different – whether it’s from Microsoft, Google or any other company. Like any cyber security measure, there are ways for skilled, dedicated hackers to bypass 2FA.
But the truth is most cyber crime isn’t all that sophisticated, and the level of skilled needed to get around this security measure is probably going be beyond most criminals. Instead, human error is likely to be a greater threat to the integrity of your 2FA.
The fact is that having to use a mobile app to log into your account every single time can quickly get tiresome. To get around this, most companies, including Microsoft, offer the ability to nominate ‘trusted devices’. These can be any computers or devices, but the idea is to choose the ones you most frequently use to sign in, and which aren’t likely to be accessed by strangers.
For instance, if you set your home computer as a trusted device, then you only have to use the Authenticator app once, to give that device access and make it a trusted device. After that, you’ll be able to log in as normal. You’ll even be able to log in automatically, if you allow your web browser to save your passwords.
The problem, as you may have guessed, is that this is potentially a major security weakness. Sure, your home computer is probably safe, but what about your laptop or tablet? What would happen if lost one of them? Mobile devices present a security risk anyway, but if you set them as trusted devices with autofilled passwords, then you’re really asking for trouble.
Of course, such problems are the result of misusing two-factor authentication, rather than weaknesses inherent to the system. A simple change in the way use 2FA would remedy this situation. For example, if you're going to let your phone autofill your passwords, rather than using 2FA every time, then make sure you set a PIN on it, or lock it with your fingerprint - anything to prevent strangers being able to access it.
Beyond Passcodes
There’s nothing to say the two factors have to be a password and a mobile device. That’s common, but there are other ways of bolstering your security. For example, you could use a fingerprint or some other form of biometric information to confirm your identity. Or you could nominate physical locations as safe zones, so you can only log in when you’re in those places.
 Biometrics offer another level of security that can be used as part of a MFA system
Biometrics offer another level of security that can be used as part of a MFA systemAnd while it’s common to use two factors, you don’t have to stop there. Two-factor authentication is just a subset of multi-factor authentication (MFA), which means you could have three, four, five or more different requirements as part of your login process. The more factors, the safer the login, but the less convenient it may be.
For organisations that deal with highly sensitive data or which operate in critical sectors, such extreme security might be worthwhile. But for most small and medium businesses, straightforward two-factor authentication, like that offered by Microsoft, offers the best mix of security and ease of use.
What Now?
If you're not already using 2FA or MFA, don't worry too much. Chances are the software and services you're already using will offer it for free; all you need to do is activate it. Just make sure you use the trusted devices feature appropriately. Do that, and you'll easily give your cyber security measures a significant boost.
TMB provides a wide range of cyber security solutions. To find out more, call 0333 900 9050 or email info@tmb.co.uk.